Xploring Xbox
A brief synopsis of my Xbox research.
Xbox Live Messaging - RCE Via Embedded Content
The Xbox messaging system supports the embedding of protocols for one-click redemption of service messages containing 5x5 game codes, viewing shared images, club invites, etc. By crafting my own service message whilst chaining another vulnerability that allowed for remote custom WinJS execution (i.e. ToastMyConsole), I was able to construct a message allowing remote code execution on any console, given the stipulation of the user interacting and clicking on the button.
{"messagetype": "Xbox/Service", "content": "{\"message\":\"Your toast is done\",\"actions\":[{\"id\":0,\"vuiGui\":\"Your Toast is Done\",\"vuiAlm\":null,\"vuiPron\":null,\"vuiConf\":null,\"launch\":\"*\",\"launchType\":\"DeepLink\"},{\"id\":1,\"vuiGui\":\"Your toast is done\",\"vuiAlm\":null,\"vuiPron\":null,\"vuiConf\":null,\"launch\":\"*\",\"launchType\":\"DeepLink\"}]}", "clientmessageid": "*", "from": "https://bn2-client-s.gateway.messenger.live.com/v1/users/xuid(*)/contacts/28:xbox_service_message", "conversationLink": "https://bn2-client-s.gateway.messenger.live.com/v1/users/xuid(*)/conversations/28:xbox_service_message", "conversationid": "28:xbox_service_message"}
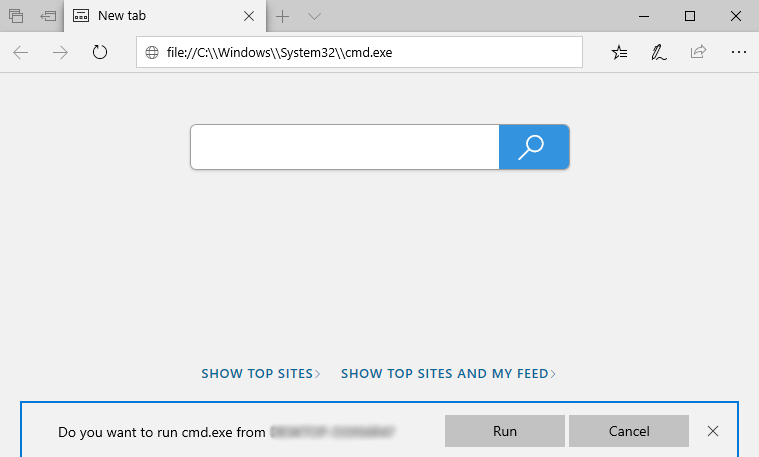
Xbox Edge Browser - File System Exposure
Edge’s address bar allowed access of local files on the device via the File:\\ protocol. This functionality is used for viewing local PDFs, etc. However, as the Xbox file system isn’t normally accessible, this allowed for the dumping of Xbox binaries. Any valid path would trigger a download prompt, copying the file to the user's download folder accessible via the File Browser application.
Side Note: The File Explorer application was disabled due to "Limited Usage"
Partner Center - Sandbox Shambles
Due to an oversight with the client-side authorization system, I was able to create and take over sandboxes belonging to publishers, essentially merging them into my account, allowing access to all of their products within said sandbox.
Microsoft Store - App Package Pulling (FE3)
By reverse engineering the Microsoft Store client, I was able to develop tools to pull packages for almost any app/game, be it internal or paid.
See my GitHub repo for a more in-depth look into the API and its capabilities.
Kiosk Mode - Abusing MSXB_KIOSK.xvd
Activation of kiosk mode is triggered on startup via the presence of "MSXB_Kiosk.xvd" on an external USB. The console will then check the XVD’s content-type to make sure it matches that of "Kiosk” before mounting. It is possible however to change the content-type of any Green-encrypted XVD to that of “Kiosk”. Renaming the modded XVD to MSXB_Kiosk and placing it on a usb will cause the console to mount the XVD on next boot, exposing the contents.
Windows Update – Ability to Pull Canary Builds
The Windows Update (FE3) service failed to perform authorization checks against the Device ID requesting a Canary build, allowing me to download IoT Canary builds for all 4 supported arches.
Xbox Flighting – MITM via Fiddler
By making use of Fiddler Web Debugger in Dev Mode, it's possible to edit incoming flighting, including enabling internal flighting, enabling various different LiveSettings, etc.
Registry path: HKLM\Xbox\Software\Microsoft\Durango\LiveSettings
Network Transfer Manager – Cross Mode Installation
By reverse engineering the network transfer manager process, I was able to develop a tool to emulate a console with NT (Network Transfer) enabled. Utilizing this, I'm able to install developer packages to Retail Mode, and retail games/apps to Developer Mode.
Service location: C:\Windows\System32\NetworkTransferManagerService.exe
Live Domain – PII Disclosure
The storage.live.com profile endpoint failed to perform authentication checks on the requesting user, allowing one to request personal details for any MSA, including name, address and OneDrive contents.
Developer Domain – App Name field vulnerable to XSS
UDC was vulnerable to XSS via crafting a specific string and setting it as the application's name, resulting in a successful cross-site scripting attack.